FREQUENTLY ASKED QUESTIONS
What benefits does the JITC certification offer?
- Compliance with DoD policy.
- Cost savings by using an established facility and process.
- Knowledgeable and experienced test personnel.
- Confidence that the application is interoperable with the DoD PKI.
- Confidence that the application is properly and securely using the infrastructure.
It is JITC policy to "Test for Success". If problems occur during the test execution, JITC immediately contacts the application owner in an effort to work through the problem.
Why does my application need testing?
The
DoD Instruction states that:
- PKE applications be tested to ensure interoperability and compatibility with the DoD PKI.
- Development authorities for PKE applications ensure interoperability with the DoD PKI in accordance with standards developed by the DoD PKI PMO.
- DoD Component Heads ensure successful completion of interoperability testing for PKE applications.
What does the certification process entail?
How long will the certification process take?
Total time is approximately 7 weeks, broken out as follows:
1 week
Application Analysis
3 weeks post test
Certification Letter Issued
What PKE application functions will be tested?
Depending on the functions performed by the specific application, the following test areas may or may not apply:
- Retrieving Certificates
- Importing and Exporting Keys and Certificates
- Storing Trust Points
- Verifying Communication Protocols
- Checking Certificate Status
- Retrieving Certificates and CRLs From the Archive
- Path Development and Processing Functions
- Application Configuration
- Application Documentation
Is my application ready for certification?
The following requirements must be satisfied (by the applications PMO/sponsor) to be considered test ready:
- PKI services are selected and requirements tailored to the needs of the application.
- Application is Public Key Enabled.
- Required operating environment for the application to securely perform its functions is identified.
- User and administrator manuals are written.
How do I request my application be tested?
Please fill out the
Request for Information Form or contact the JITC PKI/PKE Test Officer from the PKI
POCs page for further information.
Do you have a website that has information about the status of PKE application testing?
Yes, it is located at
Public Key-Enabled Application Status.
To establish direct contact with the DoD JITC PKE Interoperability Testing Team, please see the
POC page.
How to manage certificates in Internet Explorer (version 6.0 and later)
Using Common Access Card (CAC) certificates in Internet Explorer:
Open the ActivClient program. Note that depending on the version installed the screens may look different.
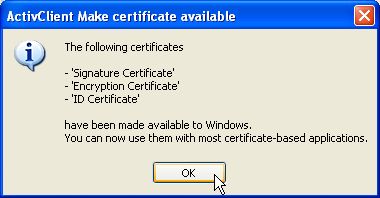
Click on Tools -> Advanced -> Make Certificates Available to Windows in the menu bar.

A message will confirm that the certificates were imported into Windows's certificate database.
Import software certificates in Internet Explorer:
Open Internet Explorer.
Click on Tools -> Internet Options in the menu bar. If you are using Internet Explorer 7.x, you may need to hold down the ALT key to display the menu.
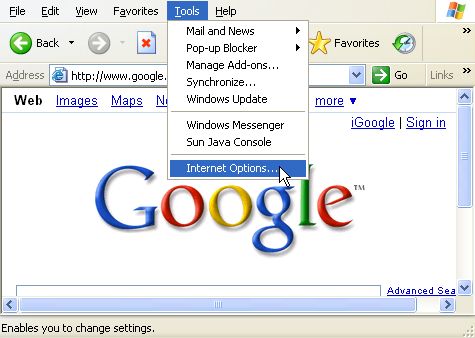
Under the Content tab, click on Certificates.

Under the Personal tab, click on Import.
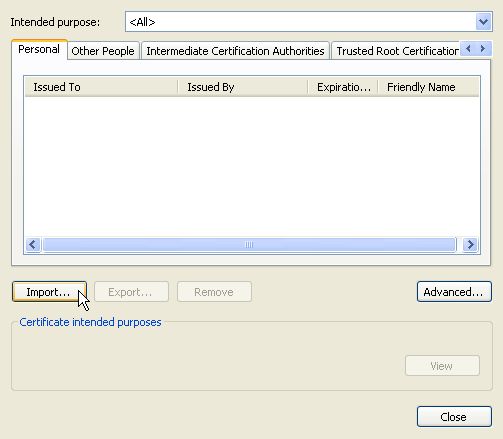
Click on Next in the Certificate Import Wizard window (not shown), then Browse in the next window.
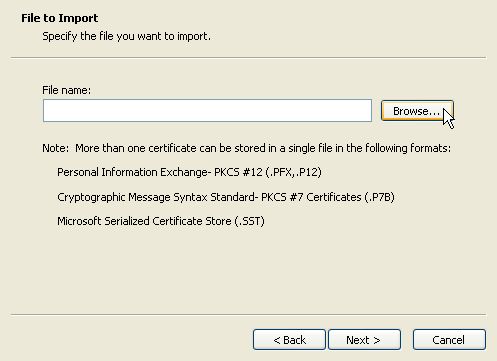
Choose the certificate backup to be imported and press Open. Note that several different file formats are accepted.
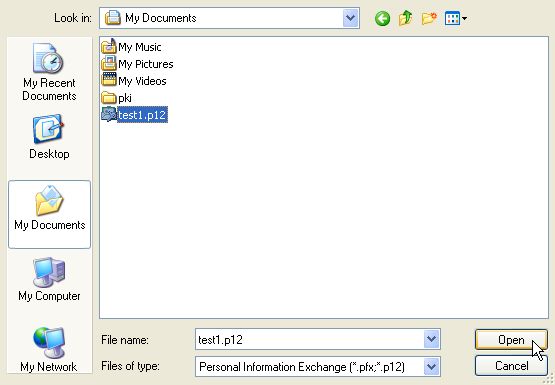
Once the correct file has been selected, press Next.
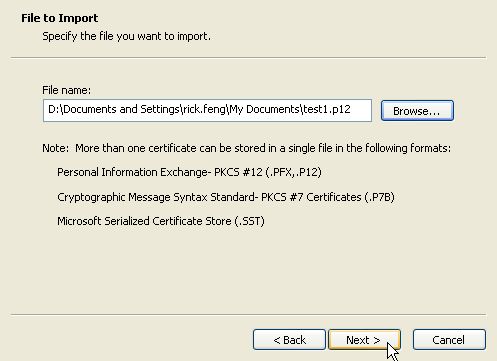
Enter the password for the certificate backup. Check "Mark this key as exportable" if you want to be able to backup the certificate later. Press Next.
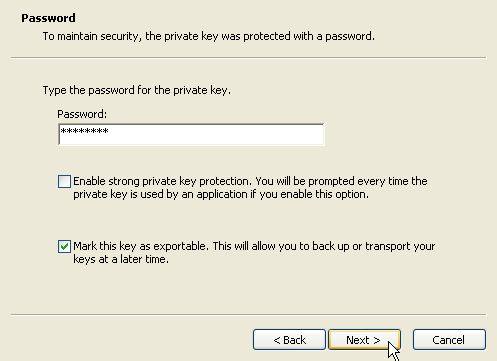
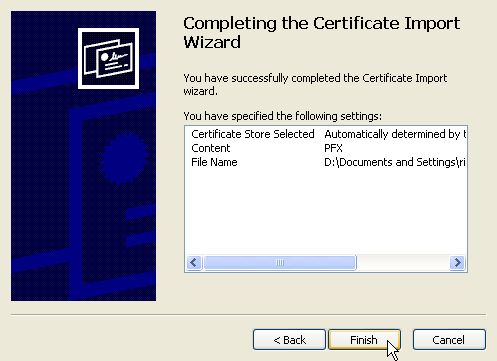
Select "Automatically select the certificate store..." and press Next.

Press Finish to complete the import.
Export software certificates in Internet Explorer:
Open Internet Explorer.
Click on Tools -> Internet Options in the menu bar. If you are using Internet Explorer 7.x, you may need to hold down the ALT key to display the menu.

Under the Content tab, click on Certificates.

Under the Personal tab, select the certificate to be exported and click on Export.
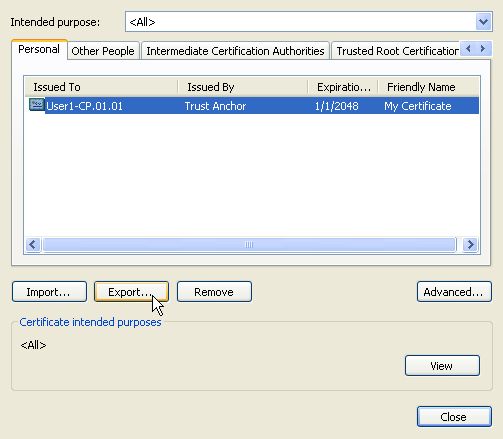
Click on Next in the Certificate Export Wizard window (not shown). In the next window, select "Yes, export the private key"and press Next.
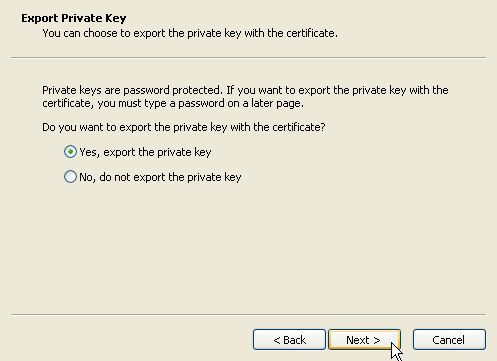
Check the appropriate options if needed and press Next.
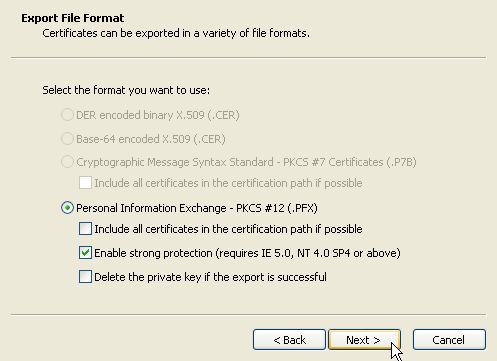
Enter a password to protect the certificate backup. Note that this password is necessary to import/restore the certificate backup later. Press OK to continue.
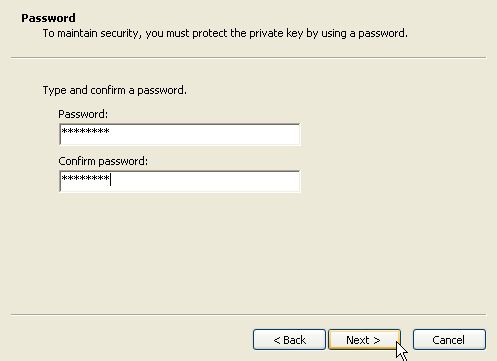
Click on Browse to choose a location to save the certificate backup, then press Next.
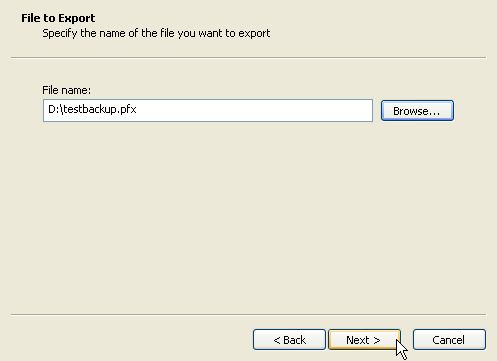
Press Finish to complete the export.
Top of Page
How to manage certificates in Firefox (version 2.0 and later)
Using Common Access Card (CAC) certificates in Firefox:
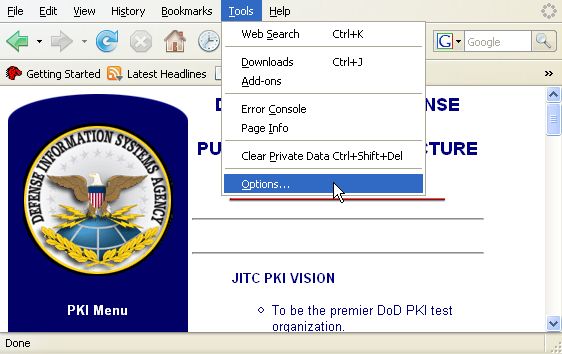
Open Firefox.
Click on Tools -> Options in the menu bar.
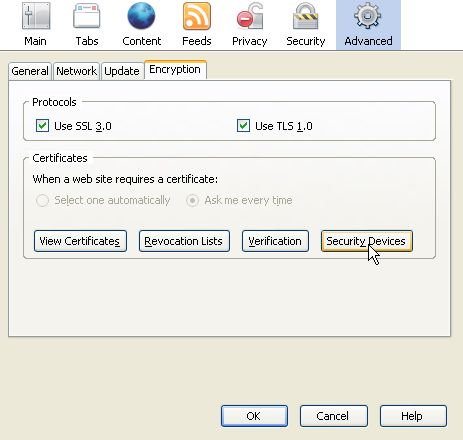
In the Options window, go to Advanced -> Encryption ->Security Devices.
In the new window, click on Load.
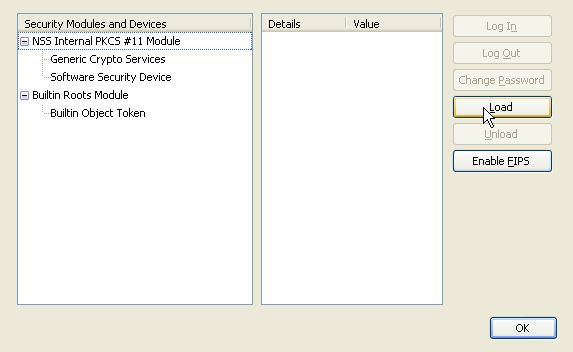
Enter "ActivClient(CAC)" for the Module Name and "c:\windows\system32\acpkcs201-ns.dll" for Module Filename and click OK, and then OK again in the confirmation window. This step assumes that the ActivClient software has been installed properly.
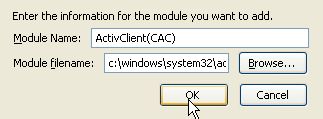
Confirmation message will show that the security device (CAC) was loaded. CAC certificates can now be used with the browser.
Import software certificates in Firefox:
Open Firefox.
Click on Tools -> Options in the menu bar.

In the Options window, go to Advanced -> Encryption -> View Certificates.
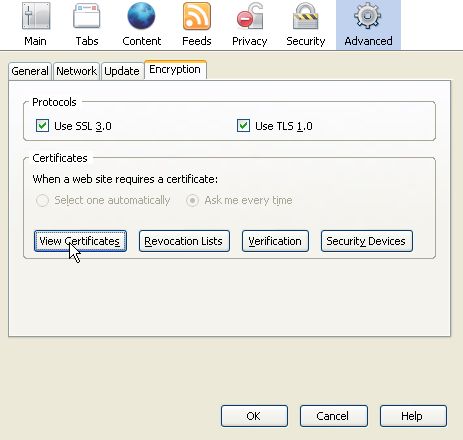
Under the Your Certificates tab, click on Import.
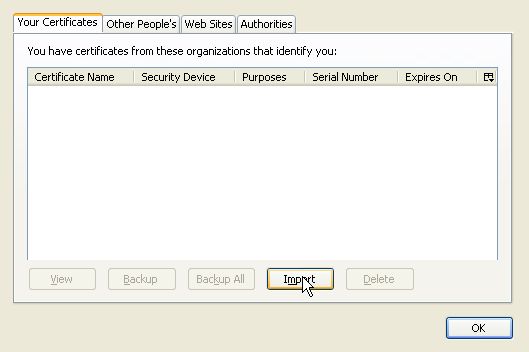
Choose the certificate backup to be imported. Note that only *.p12 files are accepted.
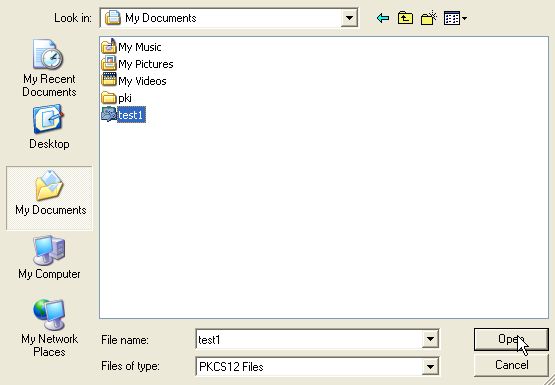
Enter the password for Firefox's certificate database (Software Security Device). Press OK to continue.
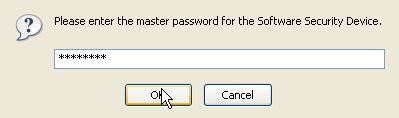
Enter the password for the certificate backup. Press OK to continue.
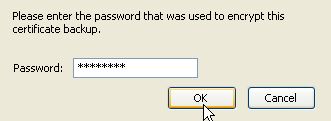
The new certificate should be displayed in the Certificate Manager.
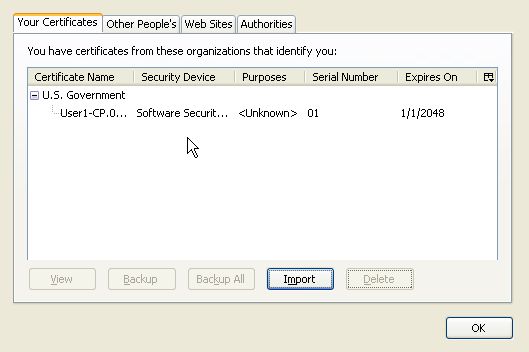
Backup software certificates in Firefox:
Open Firefox.
Click on Tools -> Options in the menu bar.

In the Options window, go to Advanced -> Encryption -> View Certificates.

Under the Your Certificate tab, select an individual certificate and click on Backup. Alternatively click on Backup All to backup all existing certificates.
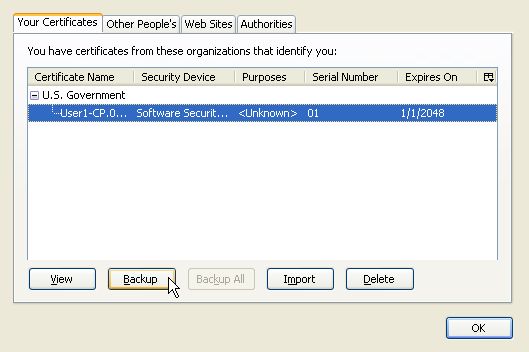
Choose a location to save the certificate backup. Press Save to continue.
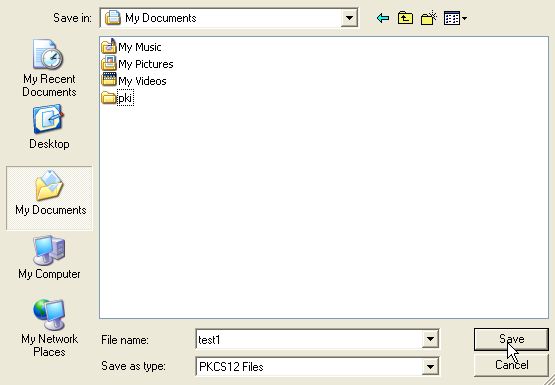
Enter the password for Firefox's certificate database (Software Security Device). Press OK to continue.

Enter a password to protect the certificate backup. Note that this password is necessary to import/restore the certificate backup later. Press OK to continue.
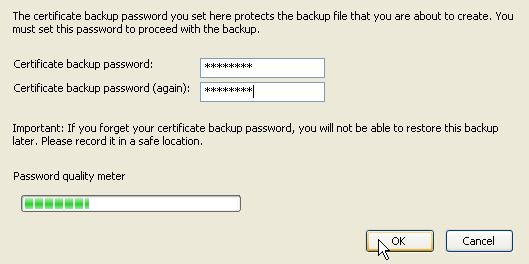
Confirmation message will show that the backup was successful. Note that certificates stored on a CAC cannot be backed up.
Top of Page
Using Common Access Card (CAC) certificates in Netscape:
Open Netscape.
Click on Edit -> Preferences in the menu bar.
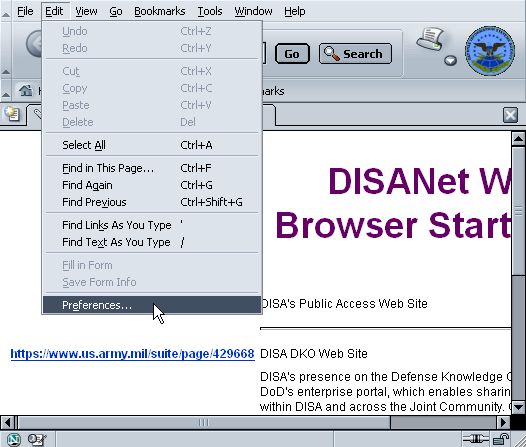
In the Preferences window, go to Category -> Privacy & Security -> Certificates -> Manage Security Devices.
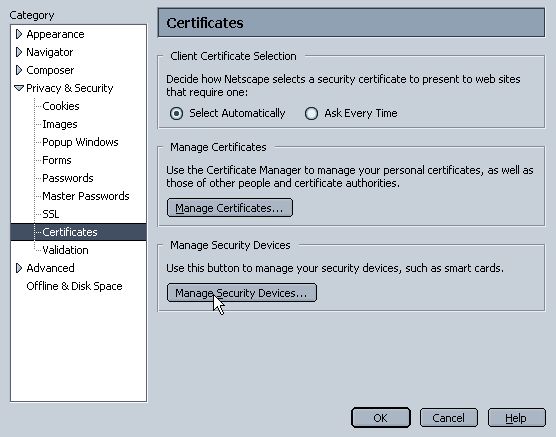
In the new window, click on Load.
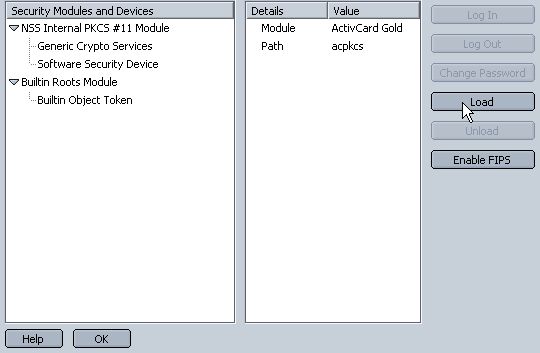
Enter "ActivClient(CAC)" for the Module Name and "c:\windows\system32\acpkcs201-ns.dll" for Module Filename and click OK, and then OK again in the confirmation window. This step assumes that the ActivClient software has been installed properly.
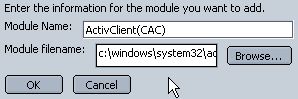
Confirmation message will show that the security device (CAC) was loaded. CAC certificates can now be used with the browser.

Import software certificates in Netscape:
Open Netscape.
Click on Edit -> Preferences in the menu bar.

In the Preferences window, go to Category -> Privacy & Security -> Certificates -> Manage Certificates.
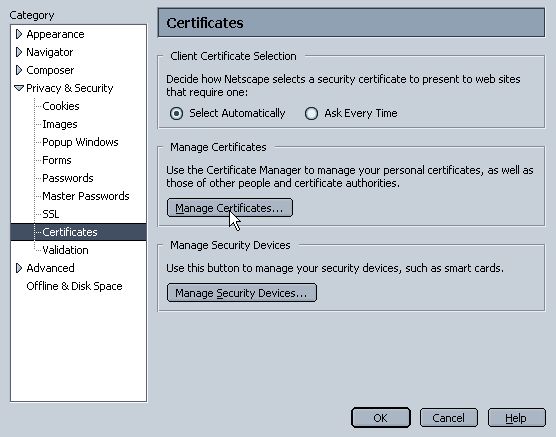
Under the Your Certificates tab, click on Import.
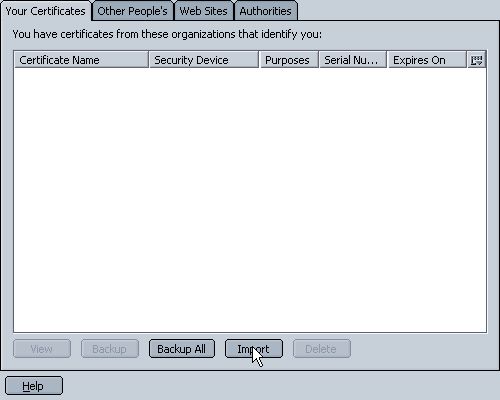
Choose the certificate backup to be imported. Note that only *.p12 files are accepted.

In the Choose Token window, choose Software Security Device in the drop down list for software certificates. Press OK to continue.
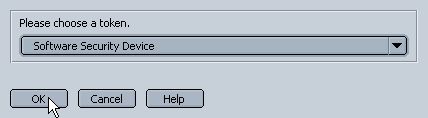
Enter the password for Netscape's certificate database (Software Security Device). Press OK to continue.

Enter the password for the certificate backup. Press OK to continue.
The new certificate should be displayed in the CertificateManager.

Backup software certificates in Netscape:
Open Netscape.
Click on Edit -> Preferences in the menu bar.

In the Preferences window, go to Category -> Privacy & Security -> Certificates -> Manage Certificates.

Under the Your Certificate tab, select an individual certificate and click on Backup. Alternatively click on Backup All to backup all existing certificates.
Choose a location to save the certificate backup. Press Save to continue.

Enter the password for Netscape's certificate database (Software Security Device). Press OK to continue.
Enter a password to protect the certificate backup. Note that this password is necessary to import/restore the certificate backup later. Press OK to continue.
Confirmation message will show that the backup was successful. Note that certificates stored on a CAC cannot be backed up.
Top of Page
How to import the DoD PKI Root Certificate:
The Army Knowledge Online (AKO)/Defense Knowledge Online (DKO) website provides instructions for installing the DoD Root Certificate. Open your Web-Browser (Internet Explorer, Firefox, or Netscape) and at the main AKO/DKO web-page, select the "How do I install the DoD Certificate?" link under the FAQs section or select the following link:
AKO/DKO Frequently Asked Questions (FAQs).
How to send an encrypted and digitally signed e-mail using Microsoft Office Outlook 2003:
Open Microsoft Outlook: Before sending an encrypted or digitally signed e-mail, the certificate must be published to the Global Address List (GAL).
Click "Start" -> "Programs", -> "Microsoft Outlook".
In Microsoft Outlook, Click on "Tools" -> Options -> "Security" tab.
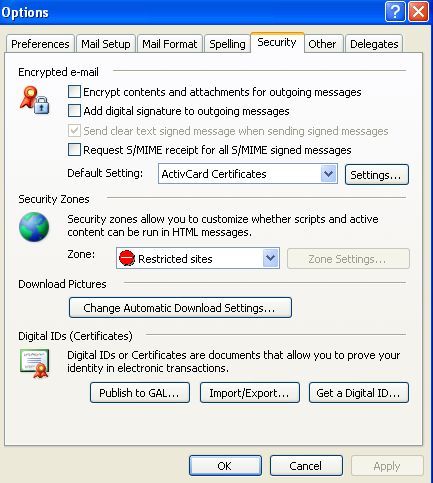
Under the "Digital IDs (Certificates)" Section, select "Publish to GAL".
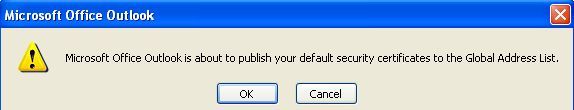
Select "OK" for the certificates to be published to the GAL. Then select "OK" to close the Outlook "Options" Window.
Select "New" -> "Mail Message". Enter "send-to" information and e-mail text. Select the "Envelope and blue lock" icon in the Outlook tool-bar (to encrypt) and/or "Envelope and Gold Seal" icon (to digitally sign). Select "Send" and when prompted, enter CAC PIN.
Top of Page
What is a certificate?
A personal certificate is the best guarantee of identity across the Internet/Intranet for the purpose of authentication, e-mail encryption, and e-mail signature. You can use personal certificates to create secure communications between agencies, across the command, or in an extranet environment.
Most modern web browsers allow you to request a personal certificate and use it to authenticate yourself to a web server. Certificate-based authentication is much stronger and more secure than password-based authentication.
You can also use your personal certificate to secure your e-mail communications. Personal certificates can be used with all major S/MIME-compliant secure mail clients, such as Microsoft Outlook and Netscape. S/MIME has been adopted by most messaging vendors as the leading mail and messaging security standard.
Identification and e-mail certificates: What's the difference?
The Department of Defense uses two certificates for secure communications across the Internet: the Identification certificate is designed as a digital identity for a user. It is used for applying digital signatures to various pieces of data and used as a more secure means of identification and authentication. The e-mail certificate is used for applying digital signatures and encryption to e-mail messages.
An Introduction to Digital Certificates:
Digital certificates are the digital equivalent (i.e. electronic format) of physical or paper certificates. Examples of physical certificates are driver's licenses, passports, or membership cards. Certificates serve to identify an individual for a certain purpose, e.g. a driver's license identifies someone who can legally drive in a particular country. Likewise, a digital certificate can be presented electronically to prove your identity or your right to access information or services on the Internet.
The same reason you trust what is stated in a military identification card: endorsement by the relevant authority (Department of Defense) in the form of a difficult-to-forge signature or stamp of approval. Digital certificates are similarly endorsed by a trusted authority empowered by law to issue them, appropriately known as the Certification Authority or CA. The CA is responsible for validating all applications for digital certificates, and once satisfied, "stamps" its difficult-to-forge digital
signature on all the digital certificates it issues, attesting to their validity.
What can I use digital certificates for?
Three uses are outlined here. Your digital certificate could be used to allow you to connect to access controlled web sites automatically without entering a user name and password. It also allows others to verify your "signed" e-mail or other electronic documents, assuring your intended reader(s) that you are the genuine
author of the documents, and that the content has not been corrupted or tampered with in any way. Finally, digital certificates enable others to send private messages to you. Anyone intercepting a message meant for you will not be able to read it!
How important is the use of digital certificates to me?
Digital certificates and the CA are just two elements of the Public Key Infrastructure (PKI), an overall Internet security system. Everyone who has a digital certificate can be traced and held accountable for their actions. Consequently, uses for the Internet, which could not be fully realized before, will finally take off, including: secure e-mail and secure web applications, on-line transactions between government agencies, and on-line transactions between agencies and vendors.
What different kinds of digital certificates are there?
Digital Certificates can be categorized into server certificates and personal certificates. The differences lie in the information they contain and who they identify.
What are server certificates?
Server certificates identify a server (computer). Hence, instead of a name of a person, server certificates contain the host name e.g. "server1.navy.mil". Server certificates are used to ensure on-line transactions are secure.
What is a Public Key Infrastructure?
PKI is that portion of the security management infrastructure dedicated to the management of keys and certificates used by public key-based security services. A PKI, if done correctly, can assure the trustworthiness of public key-based cryptographic security mechanisms.
Who should use PKI and why?
Nearly all DoD employees will need a PKI to support daily activities. These services are becoming increasingly important in networked environments where communications and transactions occur over unsecured channels. Both the needs for confidentiality and integrity (including digital signature) can be provided by cryptography, and those cryptographic mechanisms need the support of a PKI.
What are some potential uses of PKI?
Identification and authentication for purposes of gaining remote access to computers and other resources ( instead of passwords); securing financial transactions and secure messaging with confidentiality and integrity of data transmitted.
Can a user transport their personal certificate to multiple machines or locations?
Yes. A user's certificate can be exported to a floppy disk and then transported to multiple machines or locations. The certificate on the floppy is encrypted and protected with a password. You will need to import your protected certificate from the floppy disk (see FAQ on Importing Certificates).
Want to know more about Digital Certificates?
What information do Digital Certificates contain?
One of the most popular standards for digital certificates is X.509v3. An X.509v3 certificate typically contains the following information:

Figure 1: Digital Certificate format
What are the functions of a Digital Certificate?
Typically certificates are used to generate confidence in the legitimacy of a public key. In addition to verifying a signature, verifying the signer's certificate increases the confidence of the receiver that attempted forgery or impersonation has not occurred. Digital certificates can be used as to verify someone's (or some agency's) identity. It can be used in a variety of ways. Some examples include: access control to web sites, creating a virtual private network, securing e-mail, and authenticating downloaded software.
Example: A command can grant or deny access to employees, customers, suppliers, and other commands to sensitive network resources on their intranet by using digital certificates.
What is a Certification Authority (CA)?
A Certificate Authority can reside inside or outside an organization depending on the purpose of the certificates. A Certificate Authority residing inside an organization may issue certificates to personnel so that only personnel can gain access to the organization's database. A Certificate Authority residing outside an organization may issue a certificate for a user wishing to perform a secure on-line transaction.
How are Digital Certificates issued?

Figure 2: Certificate request and issuance process
Figure 2 illustrates the certificate request and issuance process by a CA:
1. The certificate applicant generates his/her own key pair and send the public key to the CA with some proof of his/her identification.
2. The CA will put the public key in a new certificate, electronically sign the certificate using its private key and then send the certificate to the applicant.
Note: The CA will check the certificate applicant's identification before it generates the certificate and signs the request. Different CAs may issue certificates with varying levels of identification requirements. One CA may insist on seeing the Identity card, another may want a signed letter authorizing certification from anyone requesting a certificate.
How do Digital Certificates work in E-mail correspondence?

Figure 3: How Alice creates a Signature
Suppose Alice wants to send a signed message to Bob. She creates a message digest (which serves as a "digital fingerprint") by using a hash function on the message. Alice then encrypts the message digest with her own private key. This encrypted message digest is called a Digital Signature and is attached to Alice's original message, resulting in a signed message. Alice sends her signed message to Bob (Figure 3). When Bob receives the message (Figure 4), he detaches Alice's digital signature from the message and decrypts the signature with Alice's public key, thus revealing the message digest. The message part will have to be re-hashed by Bob to get the message digest. Bob then compares this result to the message digest from Alice.
If they are exactly equal, Bob can be confident that the message really is from Alice and has not changed since she signed it. If the message digests are not equal, the message may not have come from Alice, was altered by someone, or was accidentally corrupted after it was signed.

Figure 4: How Alice authenticates a Signature
How do Digital Certificates work in a web site?
When a certificate is installed in a web server, it allows users to check the server's authenticity (server authentication), ensures that the server is operated by an organization with the right to use the name associated with the server's digital certificate. This safeguard's users from trusting unauthorized sites.
A secure web server can control access and check the identity of a client by referring to the client certificate (client authentication), this eliminates the use of password dialogs that restrict access to particular users.
The process that allows the identities of both the server and client to be authenticated through exchange and verification of their digital certificate is called mutual server-client authentication (Figure 5). The technology used to ensure mutual server-client authentication is called Secure Sockets Layer (SSL).

Figure 5: Mutual Authentication
- The user visits a secure web site.
- The server asserts its site identity by sending its server certificate to the client (browser).
- The user verifies the server authenticity to ensure that it is an exact site the user is visiting.
- The server requests a client certificate from the client.
- The user selects an appropriate certificate to present.
- The server verifies the client authenticity to ensure that it is an authorized user.
- When authentication is complete, the client sends the server a session key encrypted using the server's public key.
- A secure channel is established between the client and server with the following three fundamental security services:
- Services: Message Privacy, Message Integrity, Mutual Authentication
- Technology: Encryption, Keyed as functions, X.509 Certificates
- Protection: Eavesdropping, Data Tampering, Imposters
Top of Page